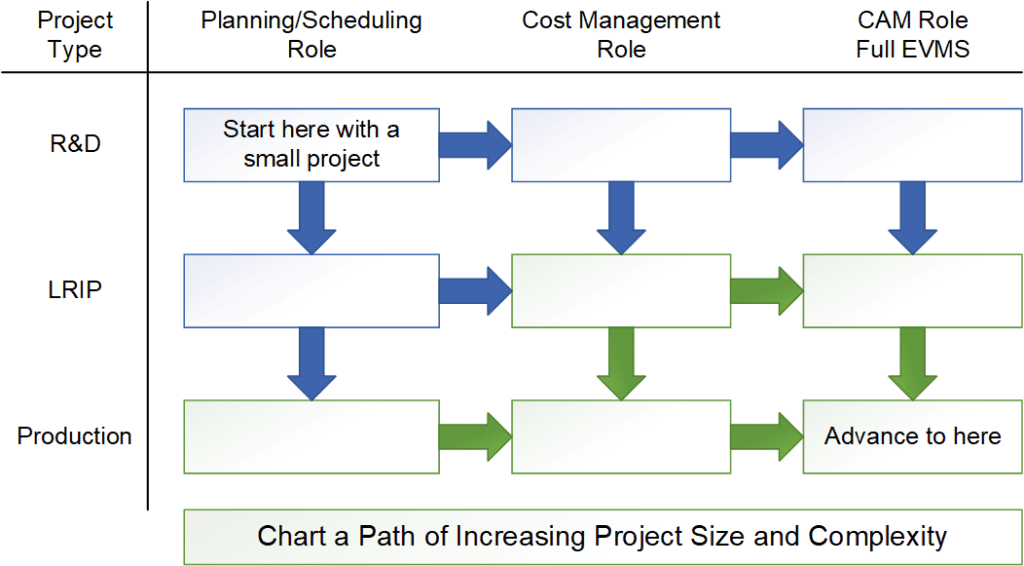
Who Should “Own” Earned Value Management (EVM)? Programs or Finance?

I have read several Earned Value Management (EVM) reports, papers, and articles that debate what company organization should “own” EVM and the company’s Earned Value Management System (EVMS). These debates most often mention the finance department and program organization as common EVM “owners.” The majority opinion seems to be that because EVM is a program management best practice it belongs in the program organization. A minority opinion is that because EVM is denominated in dollars, schedule included, and because EVM reports are financial in nature, EVM belongs in the finance department. Before we dive into this debate, a summary of the responsibilities of a Chief Financial Officer (CFO) and the head of programs is useful. In the Company A and Company B examples to follow, both the CFO and the head of programs reported to the company president.
What are the duties of a Chief Financial Officer (CFO)?
A CFO has three duties; each measured in the time domain. The first duty of the CFO is as the company’s controller and is responsible to accurately and honestly report past company financial performance. The CFO is also responsible for the current financial health of the company – to ensure that today’s decisions create rather than destroy value. And lastly, the CFO must protect the company’s future financial health and that all expenditures of capital maximize that future financial health. Every business decision, especially those of the CFO, are either good decisions (are accretive – increase shareowner value) or are bad decisions (are dilutive – destroys shareowner value).
What are the duties of the Head of Programs?
The head of programs is typically a Vice President or higher and all program and project managers report to them. The head of all programs has profit and loss responsibility for their portfolio of programs and projects. In addition, each program and project manager is responsible for achieving the technical, schedule, and cost requirements of the contracts they are executing on behalf of the company’s customers.
A Tale of Two Companies
I have first-hand experience with two companies and how each company decided who should “own” EVM that illustrates the nuances to these two approaches.
Company “A” had EVM assigned to the finance department. All EVM employees were overhead, even those assigned to a program. A new CFO arrived and quickly decided to reduce indirect costs, declaring that he was “coin-operated.” The new CFO terminated the employment of all EVM employees. Each program attempted to create an EVM branch office but failed. DCMA issued a Level 3 Corrective Action Request (CAR) detailing the EVMS deficiencies and the CFO was fired. A second new CFO arrived and agreed to transfer EVM to the head of programs. The head of programs was instrumental in changing the disclosure statement making EVM personnel assigned to a program a direct charge to that program or contract. The head of programs created a Program Planning and Control (PP&C) organization and demanded all Program Managers and their program members to quickly learn, use, and master EVM. A program control room was built with five screens. Daily 2 pm EVM data-driven reviews were held on short notice. These daily reviews became known as “CAM Bakes.” The EVM and program management culture changed quickly and dramatically at Company “A.”
Company “B” had EVM assigned to the CFO who was as “coin-operated” and unaware of EVM as was the first new CFO of Company “A.” The culture of company “B” was very hostile to EVM, so it probably did not matter who “owned” EVM. The company failed 16 of the EIA-748 Standard for EVMS 32 guideline requirements and they lost their DCMA approved EVMS status. Significant withholdings were imposed and the company’s reputation was damaged. Several top managers hostile to EVM sought employment elsewhere. A new CFO arrived who was also coin-operated – with one difference – the CFO was an expert in EVM. The new CFO formed a partnership with the head of programs. The new CFO was as much a program manager as he was a CFO. The new CFO told his direct reports assigned to each program to “make the program managers successful.” And they did exactly that.
The new CFO understood that the company was the sum of all its contracts and that every dollar flowed from its customers. The EVM and program management culture at Company “B” changed rapidly.
Who Should “Own” EVM? Programs or Finance?
Returning to our original question of who should “own” EVM, the majority theory is that the program organization should “own” EVM. All else being equal, I tend to agree with this theory.
However, while theory is suggestive, experience is conclusive. My experience at Company “A” proved that a strong program leader could rapidly change the EVM and program management culture of a company. My experience at Company “B” proved that a CFO could “own” EVM and be successful at changing the company’s EVM and program management culture. The CFO and the head of programs must form an EVM partnership no matter who “owns” EVM.
Who “owns” EVM at your company?
Mr. Kenney is a senior business executive with over 35 years of experience in the aerospace industry as well as over 10 years as a consultant to industry. He is an experienced practitioner of program management best practices as an Executive Vice President of Government Programs, Vice President of Naval Programs, and Program Manager at various aerospace and defense contractors. He is also a retired U.S. Marine Corps Colonel with 27 years of active and reserve duty.
Who Should “Own” Earned Value Management (EVM)? Programs or Finance? Read Post »